
Quick and Dirty Disaster Recovery Guide - Part I
Those hit hardest by malware and ransomware tend to be either slow-moving bureaucracies or organizations who don’t see themselves as targets.
Read More
Wisdom from the Field: Navigating the Spectrum of SOC (Security Operations Center) Services
Whether you are trying to better your security posture or want to meet compliance requirements through…
Read More
How To Avoid Business Email Compromise In Office 365
Today’s successful SMBs (small to medium-sized businesses) edge out competitors by employing both technology…
Read More
Realistic Data Security for SMBs, Part 1
It’s a tired line: vet your vendors. For security professionals who find themselves playing this song…
Read More
True Digital Security Continues Annual Tradition of Volunteering for Tulsa's United Way Day of Caring
TRUE employees enjoyed volunteering together at the Westside YMCA for this year’s Tulsa Area United…
Read More
True Digital Security Achieves AWS Solution Partner Status
Industry leader in information security becomes newest AWS Solution Provider Partner WEST PALM BEACH,…
Read More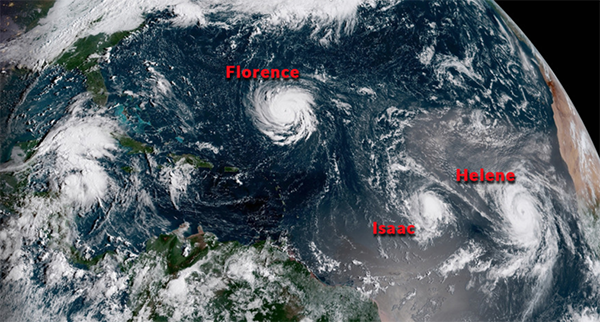
Hurricane Florence: Remain Vigilant, Be Prepared, Stay Protected
While we are past the midway point of hurricane season, which runs June 1 through November 30, this is…
Read More
New Developments and Deadlines for PCI DSS: PCI DSS 3.2
The February 1, 2018 new requirements date for PCI DSS 3.2 has come and gone. The February 1 deadline…
Read More
True Digital Security Extends Reach Via Advanced Vision Technology Group
FOR IMMEDIATE RELEASE TRUE DIGITAL SECURITY EXTENDS REACH VIA ADVANCED VISION TECHNOLOGY GROUPIndustry…
Read More
How To Defend Against Pass-the-Hash Attacks: Part II
Welcome to Part Two of Defending Against Pass-the-Hash attacks straight from your favoriate penetration…
Read More

