
What is the Best Phishing Defense? A Good Offense.
The cost of a phishing attack is high. In 2015, the average 10,000 employee company spent $3.7 million…
Read More
Why SIEM Deployment Is So Difficult
Many organizations are attempting to deploy a SIEM (Security Information and Event Management) capability,…
Read More
What Is the Difference Between EMV and PCI Compliance?
It might be a surprise to some that EMV (Europay, MasterCard, and Visa) compliance is not associated…
Read More
What the Meltdown and Spectre CPU Vulnerabilities Mean to You
Meltdown and Spectre require that you put aside standard maintenance schedules and weekly patching windows…
Read More
True to Present at Information Warfare Summit 10 Conference
You won’t want to miss True’s sessions at the upcoming Oklahoma Infragard Information Warfare Summit…
Read More
True Day of Caring 2017
Our True team had an excellent time at the Tulsa Area United Way Day of Caring this year, building privacy…
Read More
New Employee Announcement
In our industry, roles are constantly being redefined and revolutionized. TRUE believes in constant innovation…
Read More
PCI Guidance for Penetration Testing & Mobile Payment Applications: Sept 2017
Last week, the PCI council published updated guidance on Penetration Testing and Mobile Payment Applications. …
Read More
How To Spot & Avoid Credit Card Skimming
Credit Card Skimming FAQs What are credit card skimmers?There are many ways thieves can steal your data…
Read More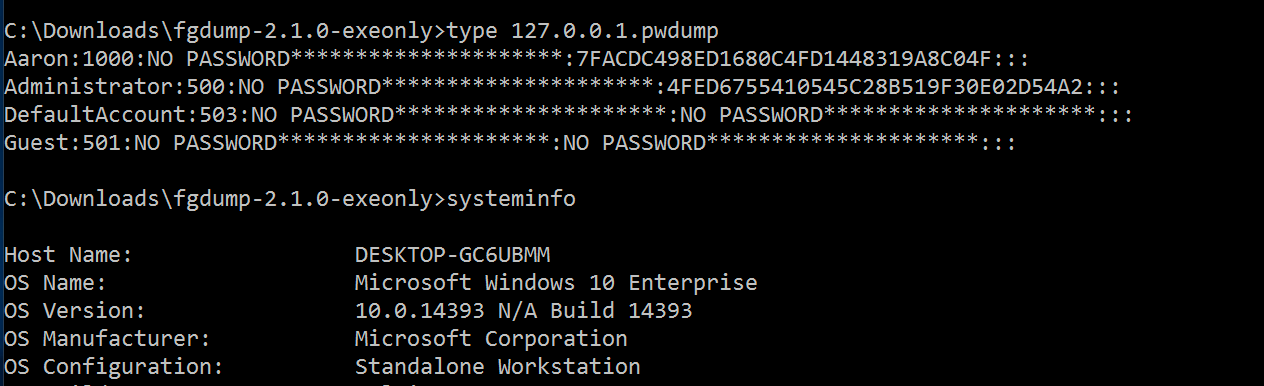
How To Defend Against Pass-the-Hash
What Is Pass-The-Hash? Pass-The-Hash (PTH) is an attack designed to allow an unauthenticated attacker…
Read More

