
True Proudly Supports TU's CTF and CCDC Teams
True is honored to support the Tulsa community. Since we opened our doors in 2004, that support has taken…
Read More
Day of Caring 2015
For this year's Tulsa Area United Way Day of Caring, True volunteered at the Girl Scouts of Eastern Oklahoma's…
Read More
The DEFCON 2015 Experience - The Interns' Perspective
What is a "hacker"? Over the years the media has twisted the meaning, so that today it is widely used…
Read More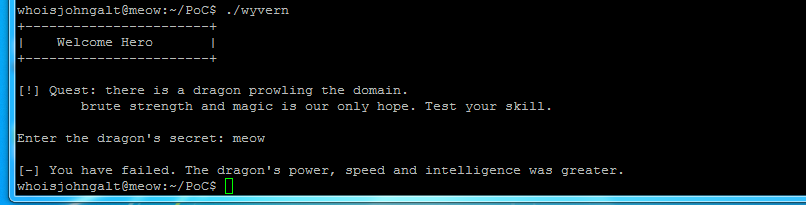
CSAW: Reverse Engineering for 500, Please.
Toward the end of July, FireEye released a set of CTF-style challenges for their second annual FlareOn…
Read More
CSAW 2015: Crypto 500 - Bricks of Gold Writeup
This past weekend I participated in the CSAW 2015 CTF on team ascii_overflow. Our team is relatively…
Read More
Mitigating Spear Phishing through Increased Awareness
To carry out ethical spear phishing attacks in order to help organizations test their security awareness…
Read More
Capture The Flag (CTF) Competitions
In the cyber-security realm, arguably one of the best methods of gaining hands-on experience is to compete…
Read More
POODLE Attack on SSL 3.0
The POODLE attack or "Padding Oracle On Downgraded Legacy Encryption" is a fairly recent attack that…
Read More
TLS & SSL Protocols
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are cryptographic protocols that are designed…
Read More
Logjam Vulnerability
The TLS protocol is the current standard for secure communication over the Internet and until now had…
Read More

